IoT | Free Full-Text | Evaluation and Selection Models for Ensemble Intrusion Detection Systems in IoT

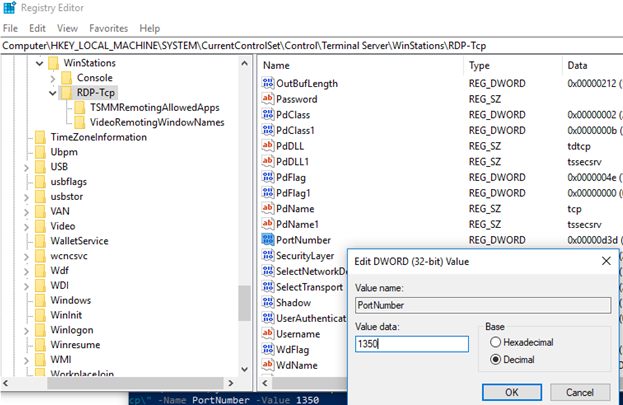
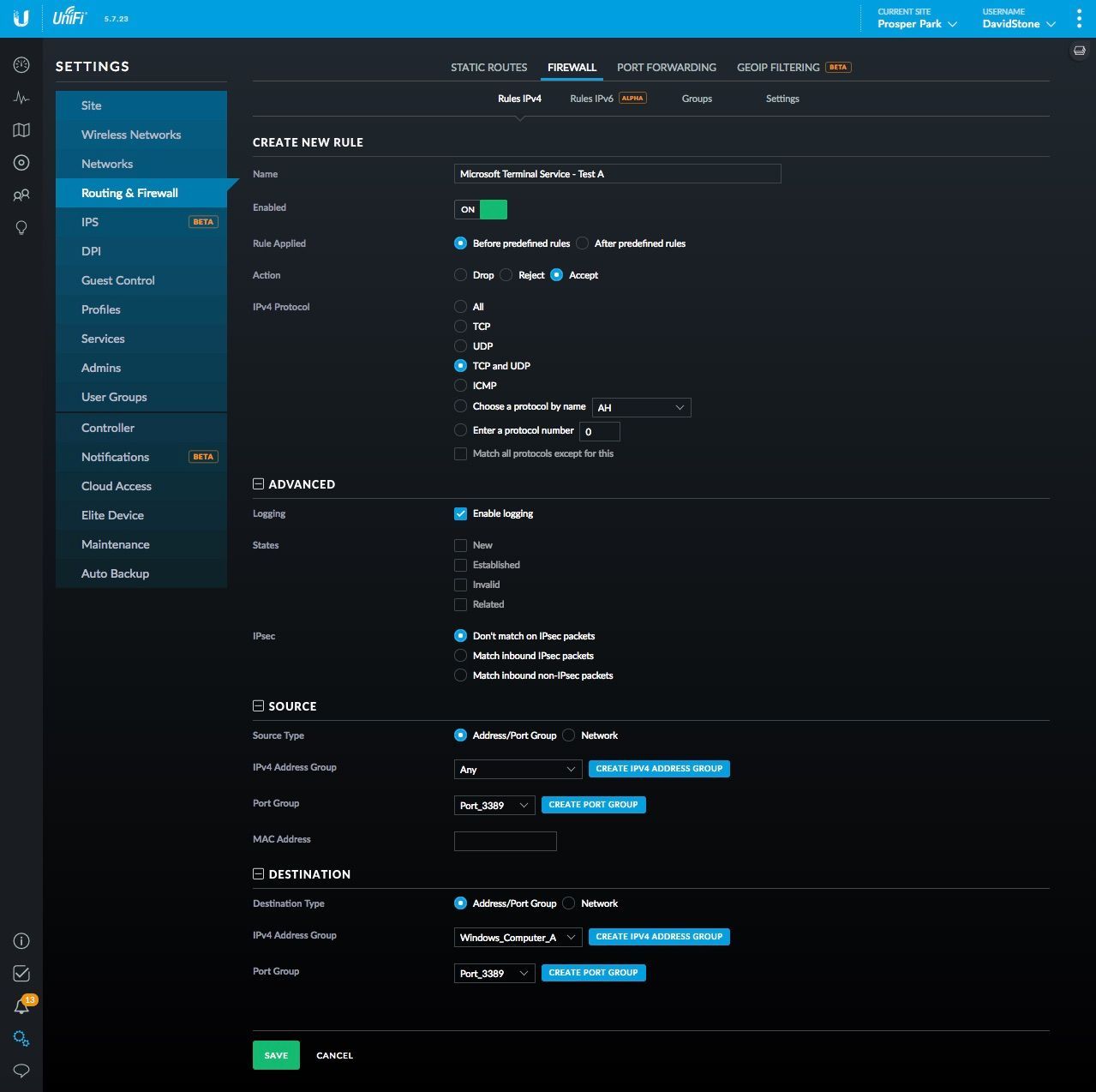
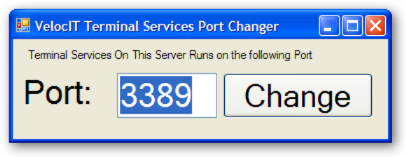
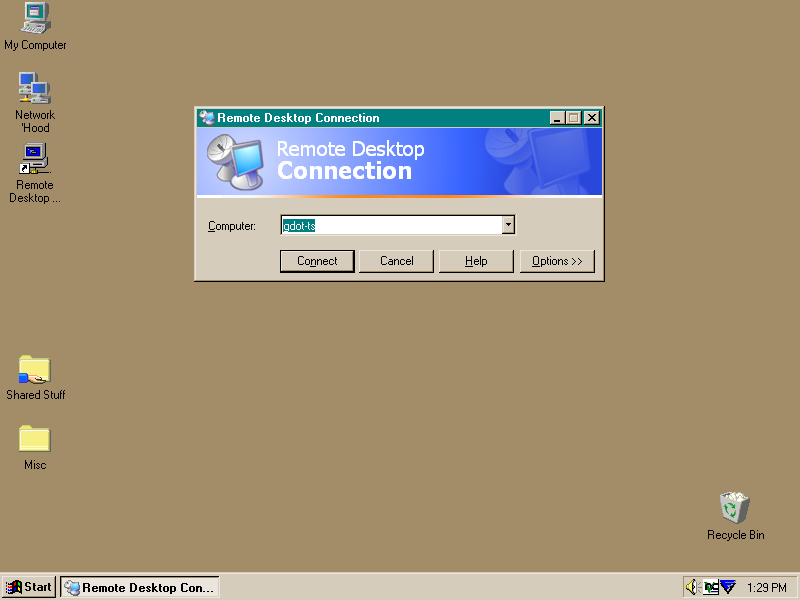
How to Map a Different Listening Port for Remote Desktop Protocol | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More

How to Map a Different Listening Port for Remote Desktop Protocol | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
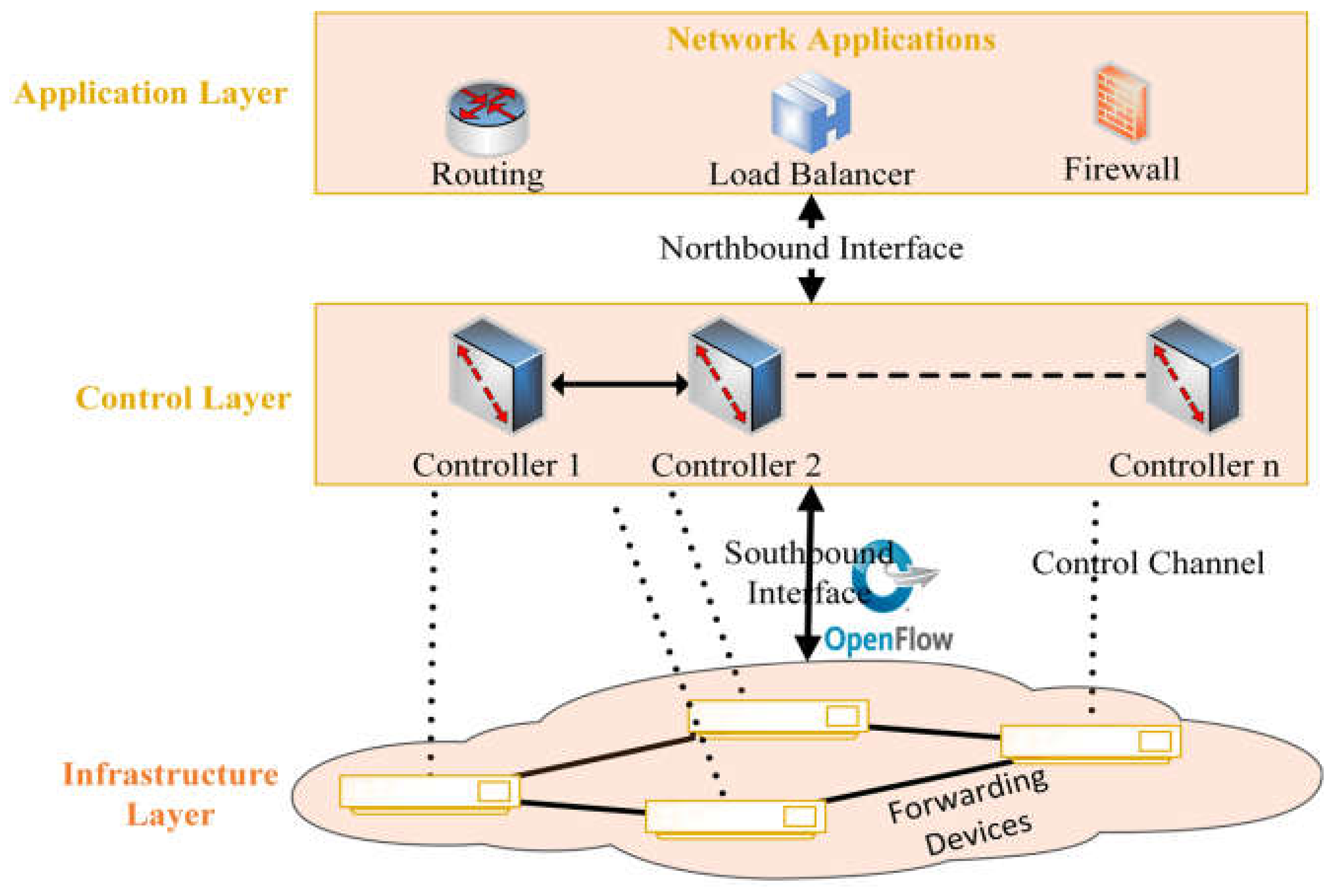
Applied Sciences | Free Full-Text | SDN-OpenFlow Topology Discovery: An Overview of Performance Issues
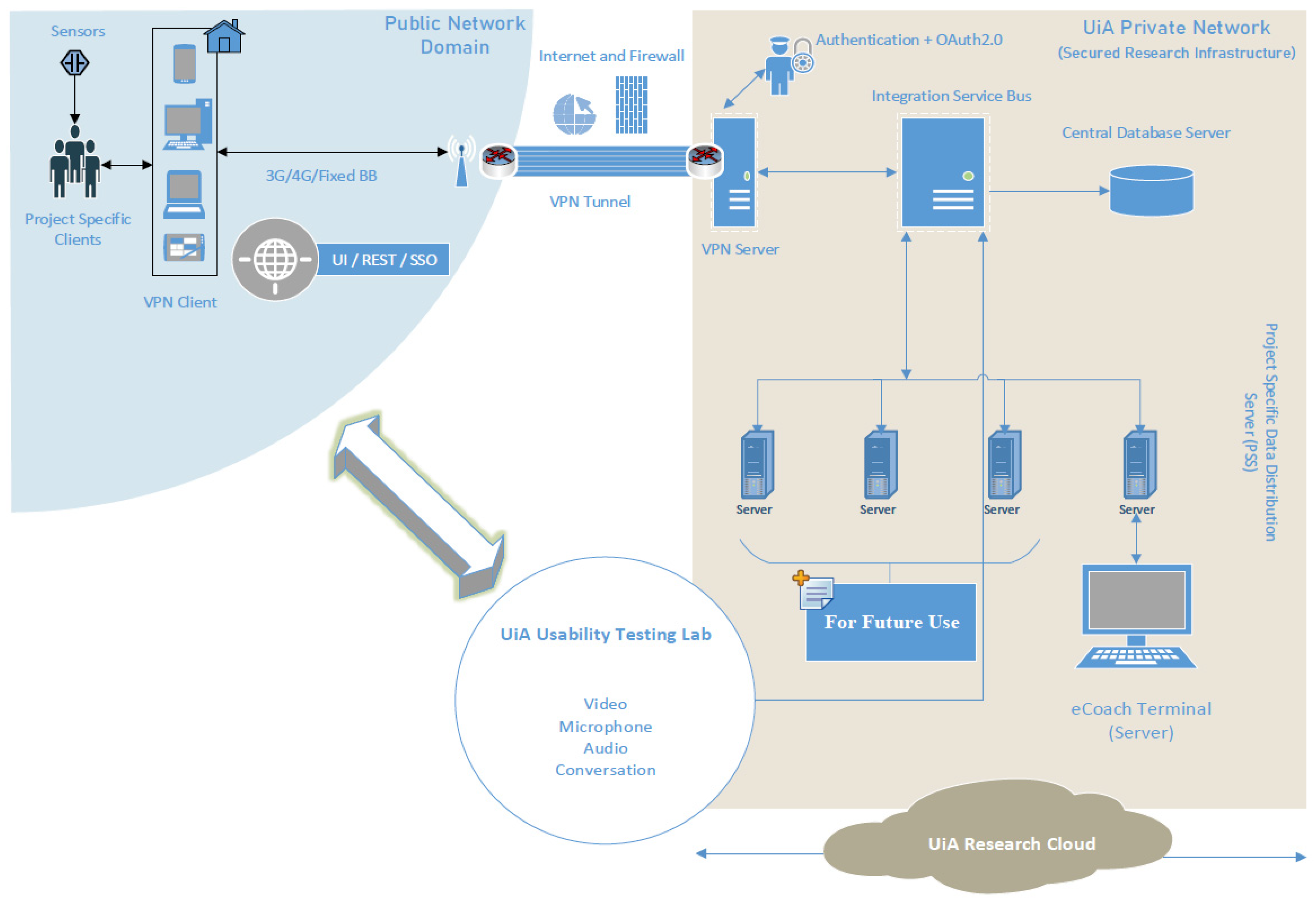
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study