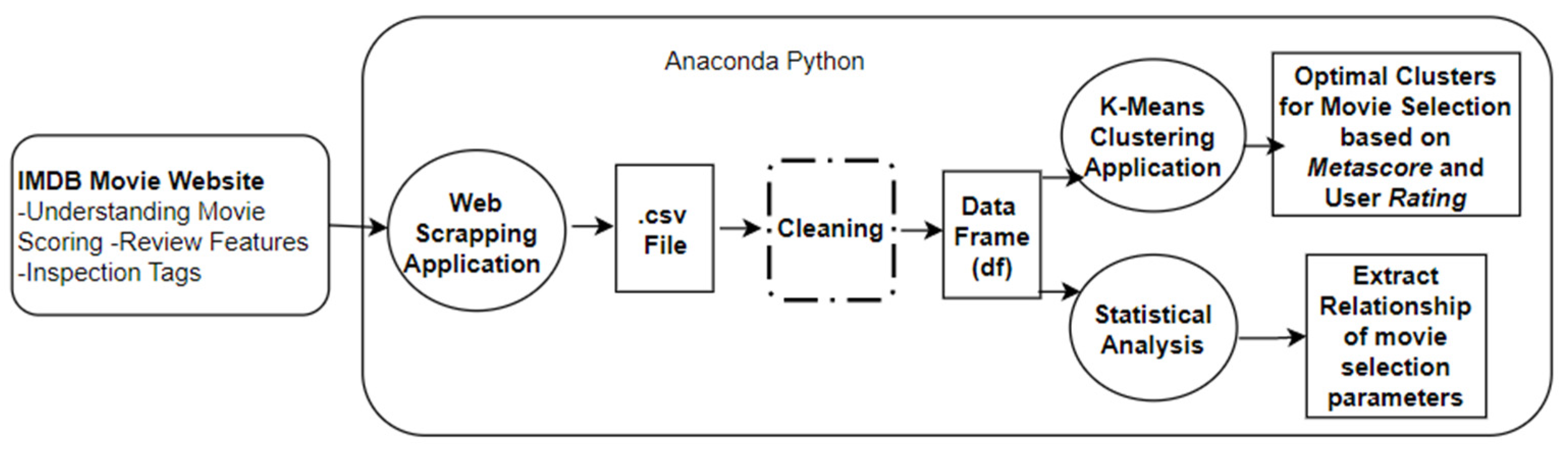
Computers | Free Full-Text | A Ranking Learning Model by K-Means Clustering Technique for Web Scraped Movie Data

APT34 Event Analysis Report - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

APT34: The Helix Kitten Cybercriminal Group Loves to Meow Middle Eastern and International Organizations | Blog
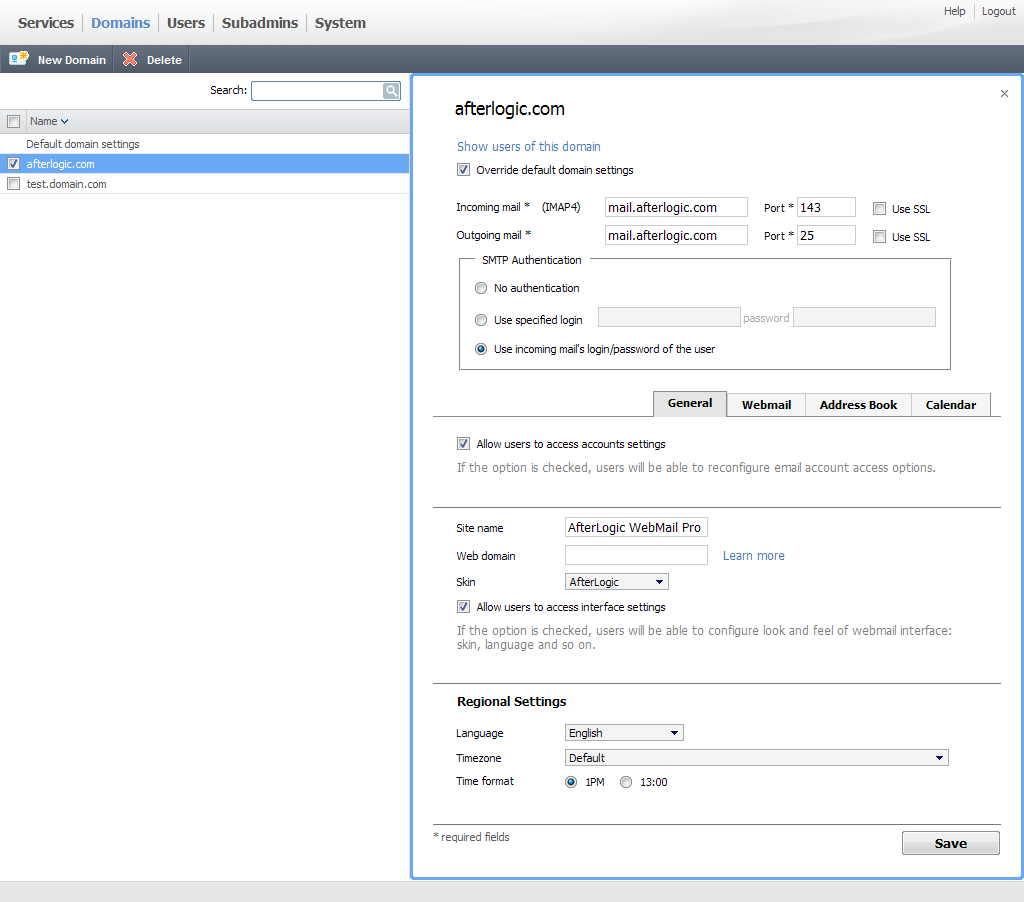
Automated Malware Analysis Report for http://go.pardot.com/webmail/869541/338720277/d7f2a5765375dd55b7c7a12c5c0f6bc2e94d030f255f5a0f44e50cf303e402f3 - Generated by Joe Sandbox

APT34 Event Analysis Report - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
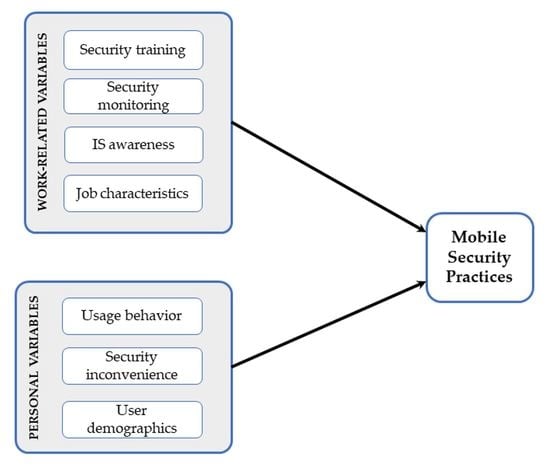
Applied Sciences | Free Full-Text | Predictors of Employees’ Mobile Security Practice: An Analysis of Personal and Work-Related Variables